It gets worse; even after a file is overwritten while saving more files to your hard drive, it might still be recoverable if enough fragments of the file exist and the person making a recovery has the right technical know-how and tools. We’ve previously covered how to use CCleaner to delete files securely. Today we’ll cover seven other free tools for Windows that help you securely erase data from your hard drive so it can’t be recovered. Several of these tools are portable and can be stored on a USB flash drive. Portable secure erase tools are useful if you often use public computers. Some of these tools also allow you to securely wipe the free space on your hard drive, making any files and folders you erased without using a secure method unrecoverable.
1. Eraser
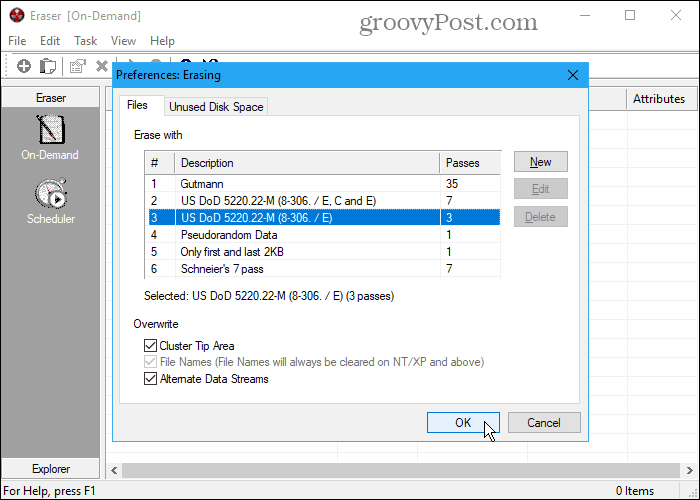
Eraser is a free tool that allows you to completely and securely delete sensitive data from your hard drive. It overwrites the data several times using one of six methods, including the US DoD 5220.22-M standard with three passes or seven passes and the Gutmann method with 35 passes. Go to Edit > Preferences > Erasing and select the method on the Files tab. You can even add your own custom methods. Be aware that if you select the Gutmann method in Eraser (or in any of the other tools listed below), the secure deletion process may take a long time. Add files to Eraser to delete them immediately using the On Demand interface. Or use the Scheduler to automatically securely delete the selected files at a later time. If you don’t want to install Eraser, download the portable version of Eraser. You won’t get the right-click menu option in File Explorer. But you still get the On-Demand and Scheduler features for securely deleting files and folders in the software. You can also integrate Eraser into File Explorer, allowing you to select files in Explorer, right-click on them, and securely erase them. To do this, you must use the installable version of Eraser.
2. Secure Eraser
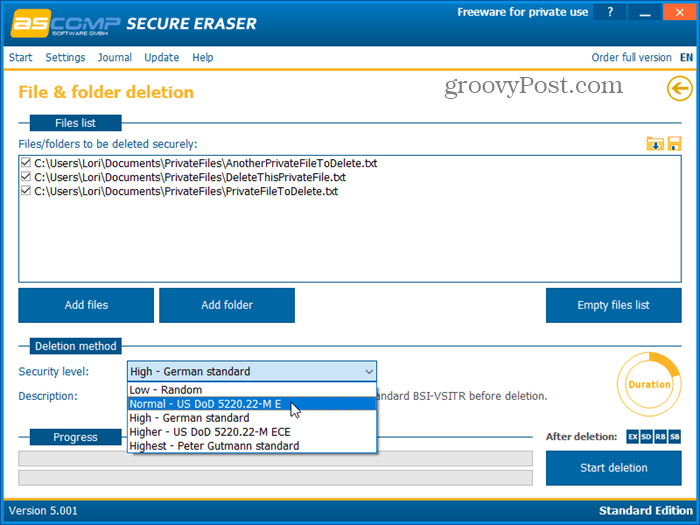
Secure Eraser is an easy-to-use program that allows you to securely erase data from your Windows computer using one of five different security levels. Your data will be overwritten up to 35 times, making it unrecoverable, even with specialized software. Select the Security level you want under the Deletion method. The Report administration feature maintains a log of all operations and generates a detailed report displayed in your default browser. You can also use Secure Eraser to delete a drive or partition securely and securely wipe the free space on your hard drive or even to clean the registry or your system. When you use the free Standard Edition, you’ll be prompted to buy the full version after each deletion. But, if you don’t mind seeing the message every time, you can continue to use the free Standard Edition for personal use. To remove the message, purchase the Professional version for $20 for a private license or $40 for a company license.
3. Freeraser
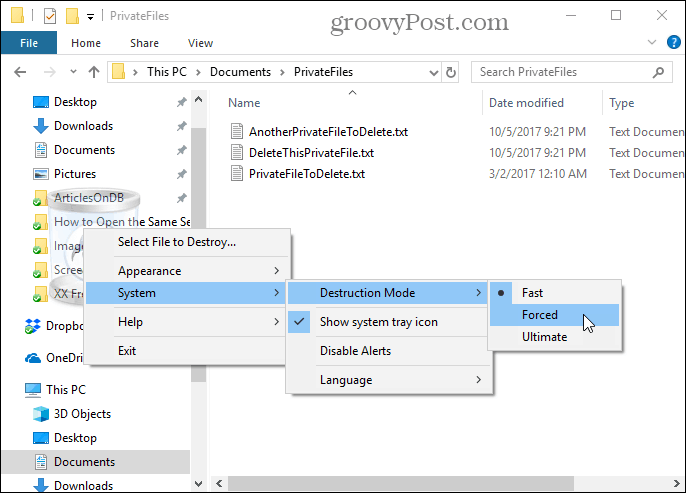
Freeraser is a free, portable tool that allows you to securely delete files directly in File Explorer using drag-and-drop. When you run the program, you’ll see a trash can icon on your desktop that sits on top of all other windows. Drag your files and folders to the icon to securely delete them. Right-click on the icon to manually select files to destroy, change the Appearance, or change System settings like the Destruction Mode. The program offers three destruction modes for securely deleting your data. The Fast method overwrites the files once with random data. To overwrite the data three times according to the DoD 5220.22-M standard, select Forced. Selecting the Ultimate method overwrites the deleted files and folders 35 times according to the Gutmann method.
4. File Shredder
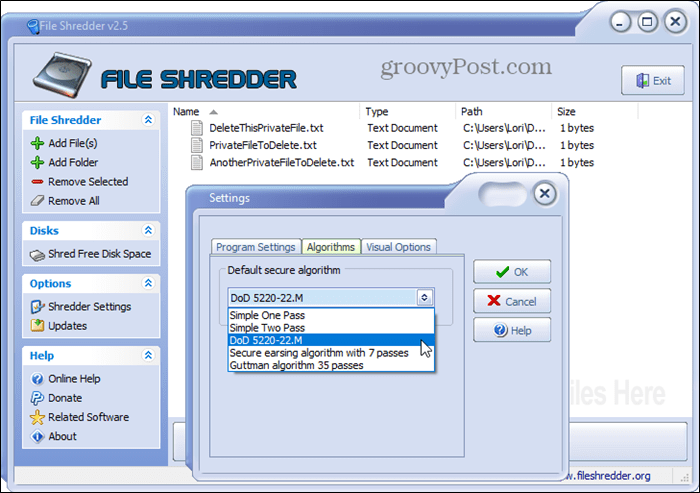
File Shredder is a free, straightforward program that allows you to erase files securely and securely wipe free disk space. The program provides five different methods for securely deleting files that include one pass, two passes, the DoD 5220.22-M method (three passes), 7 passes, and the Gutmann algorithm (35 passes). Go into the Shredder Settings and select one of these options on the Algorithms tab. You can also integrate File Shredder into File Explorer. This allows you to select files and folders to delete them in Explorer, right-click on them, and securely delete them from the context menu. Go into the Shredder Settings and check the Enable Shell Integration box on the Program Settings tab.
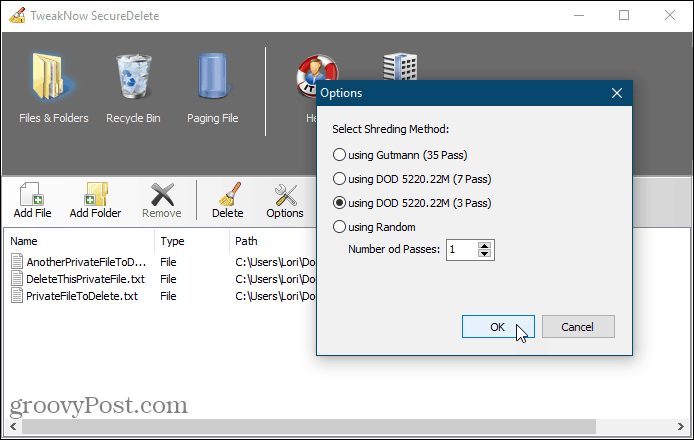
5. SecureDelete
SecureDelete is an easy-to-use free program that allows you to securely delete files and folders using one of four shredding methods. You can choose one of the DoD 5220.22-M methods (3 passes or 7 passes), the Gutmann method (35 passes), or overwrite the deleted files and folders with random data using a custom number of passes. Click Options to select the method you want to use. Then, click Add File to add one or more files or Add Folder to add an entire folder to the list. To delete the added files or folders, click Delete. If you’ve deleted some files normally and they’re still in the Recycle Bin, you can securely delete those files too. Click the Recycle Bin icon in SecureDelete and then click Empty Recycle Bin. Windows uses a paging file on your hard disk as additional backup memory when you have no more physical memory left. But, unlike physical memory, the paging file is not automatically cleared when you shut down your computer. It remains available, and anyone with enough know-how can access the data in the paging file. SecureDelete offers an option to clear the paging file automatically when you shut down your computer. To set this up, click Paging File and select Enable from the Clear paging file at shutdown drop-down list. Then, click Save. Restart your computer to finish applying the change.
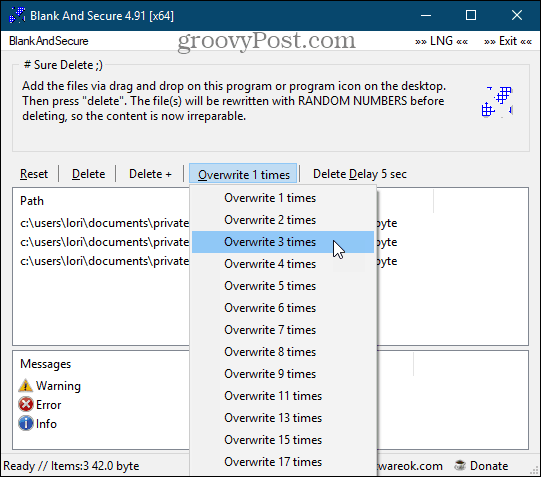
6. Blank And Secure
Blank And Secure is a free, portable tool for securely deleting files. Before deleting your files, select the number of times you want to Overwrite the files with random numbers. They don’t use the DoD 5220.22-M and Gutmann methods. You can also choose a Delete Delay of up to nine seconds. Drag and drop the files or folders you want to delete onto the program window and click Delete. Use the Delete + button if you want to end the program, shut down your PC, put your PC in standby mode, or end the program and put the PC in standby mode after securely deleting the files. Click Reset if you decide not to securely delete the selected files and folders and want to remove them from the program.
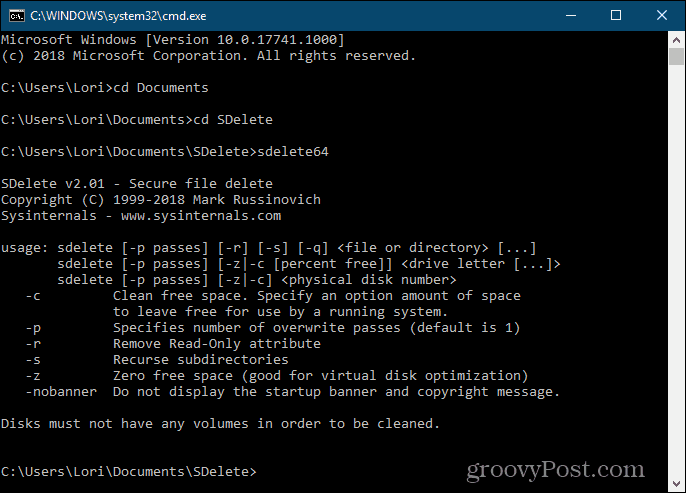
7. SDelete
For those of you who like using the command line, we have SDelete, one of Microsoft’s Sysinternals tools. The program uses the Department of Defense clearing and sanitizing standard DoD 5220.22-M. You can specify how many passes you want SDelete to perform when it deletes files and directories. The default number of passes is one. SDelete is portable and can be run from a USB flash drive. In File Explorer, open the folder containing the extracted SDelete program files. Then, to open a command prompt window to the current folder, type: cmd.exe in the address bar in File Explorer and press Enter. To get instructions on using the command, type: sdelete or sdelete64 (depending on whether you’re running a 32-bit or 64-bit version of Windows, respectively) and press Enter.
Secure Your Data, Even When Deleting It
Secure delete tools are as important as other tools that protect your privacy, like password managers (for example, KeePass and 1Password) and VPNs and getting in the habit of creating strong passwords. Decide which tool is your favorite and keep it handy for deleting your private and sensitive data. Do you like the secure delete tools we listed here? Have you found any other tools for securely deleting files? Please share your thoughts and findings with us in the comments below! The OS may have taken copies of the file within such processes as System Image or other partition or drive backup facilities. And that may be held in a ‘Shadow storage’ location, rather than any folder you know about, or even have access to as a file within a folder. The OS may have made multiple copies of the file, and any intermediate, or prior versions of the file including File-History, and office (or similar apps unsaved file recovery facilities – in whatever folder they have been set to use – by default or user settings. Apps may have been installed to copy ‘recoverable’ instances, or backup versions or just access from other devices to cloud storage – not just as you specifically direct, but also as part of ‘sync’ processes or just remote access The hardware may have been set to image the folder (or partition) containing the files. You may have a SSD that is modern enough to have extra storage over that set for access as the partition – and it may have swapped the storage that contains your file out of the storage that the OS considered part of the partition at the time you specify erase for the file – An ‘Erase’ app will usually overwrite the assigned storage locations several times – but the SSD may well be swapping the indicated storage out of the previously assigned storage location each time the ‘erase’ App asks the OS to write to that storage – That is under the control of the storage device not the OS, or the App. You may have set the OS to use an app to take a backup of the partition, or folder(s) to an external storage device – USB connected hard drive, or home cloud facility. And – considering the clear the pagefile at closedown – well… the OS may well have (OK will usually have) expanded the pagefile while running processes, and then contract it when the apps no longer appear to need the additionally acquired space – so the content of the file that was in memory to be edited may well have been written to many blocks of the storage that were temporarily made part of the pagefile, and have now been released – so any ‘Erase’ App that wipes the pagefile will not actually be able to determine where the data is on the storage – or even if the storage device (SSD) will allow it to access that portion of the storage. So – basic assumption should be that – YOU have to be very careful what storage device you use for any ‘sensitive’ data, and what your system allows to access the data, and what devices IT could access for temporary or permanent storage of the data – and consider any SSD that has not been destroyed to contain recoverable versions of the data that was put on it – that is as long as any of the RAM is electrically viable, unless you have acquired and run some ‘clear the storage’ program from the manufacturer. Basically – for me – peace of mind would only be achieved if a hard drive had the platters shattered, and a ‘memory’ based device had been well cooked – by temperature, or electrically – EMP would possibly, OK probably do the job. OK – Paranoia rules – But are you sure that the government, or your siblings/mates have not already copied the data ? Comment Name * Email *
Δ Save my name and email and send me emails as new comments are made to this post.
![]()